Assessment for Supply Chain Threats
Next-Gen Risk Intelligence for a true holistic assessement in Realtime
A First-of-its-kind Solution to assess and control risks from vendors in real-time, stopping cyber threats before they breach your defenses.


first-of-its-kind solution (NIS-2)
The Art of Anticipation
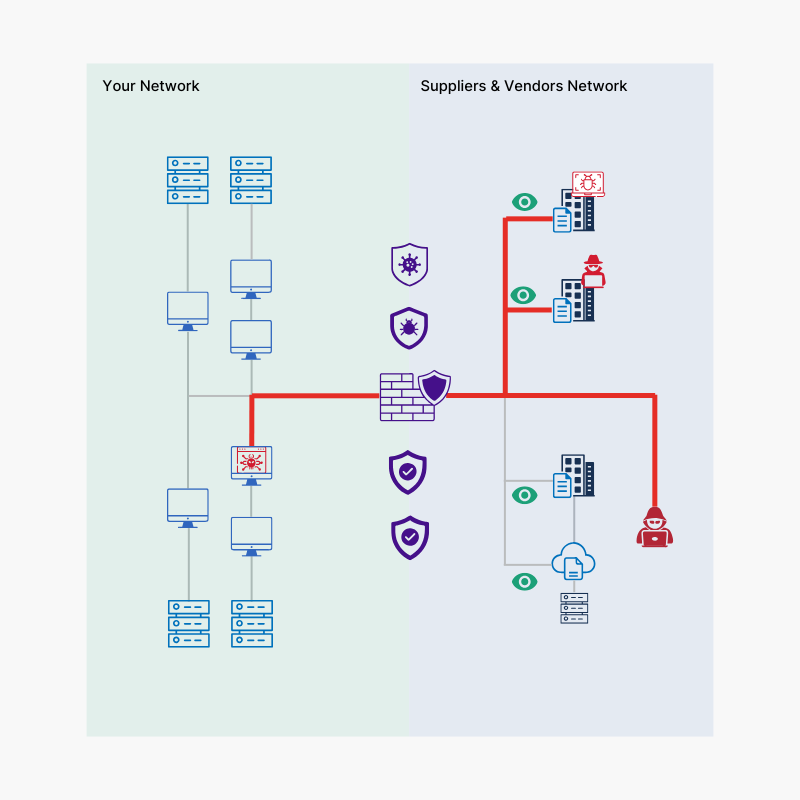
Companies struggle to see and manage cyber risks across complex supplier and cloud networks. With hidden vulnerabilities in supply chains and limited visibility into third-party security, organizations are left exposed to unseen threats.
So cybercriminals increasingly targeting suppliers as it is the easiest route into larger companies.
Our offered Solutions bridges this gap, offering the clarity needed to understand and mitigate these risks effectively.
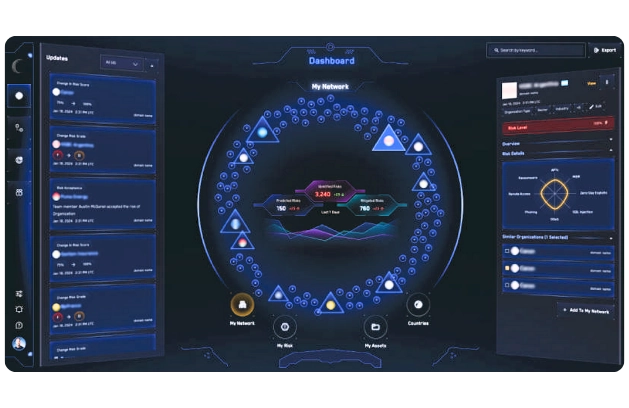
TRUE REALTIME RISK ASSESSMENT
Key Benefits
Instead of focusing merely on risk value calculation that is based on public leaks, vulnerabilities, open ports & services, or any other insufficient vectors – we rely on intelligence-led insights right from adversarial sources.
Risk Assessment based on facts and real-life incidents
Pinpointing the cyberattack’s root cause, providing and advantage over the defenders and affected organization’s supply chain network.
A fully covered threat landscape
Every notorious adversary or other APT is instantly visible in the system, accurately calculating the victims’ risk value before any attacks takes place.
Accurate display of blind spots and NSB observables
Weak links, vulnerabilities or any blind spots that normally go unnoticed will be avaliable for you to see. Ensuring your reilience on all fronts.
Comprehensible and timely risk values
Risk values are thoroughly explained, providing clear and concise data. Sharing details on why, what and when. 3A Intel: Accurate. Agile. Actionable.
Early warning system
Early Warnings regarding future attacks withing the platform ensures that you are well-informed about any compromies heading your way.
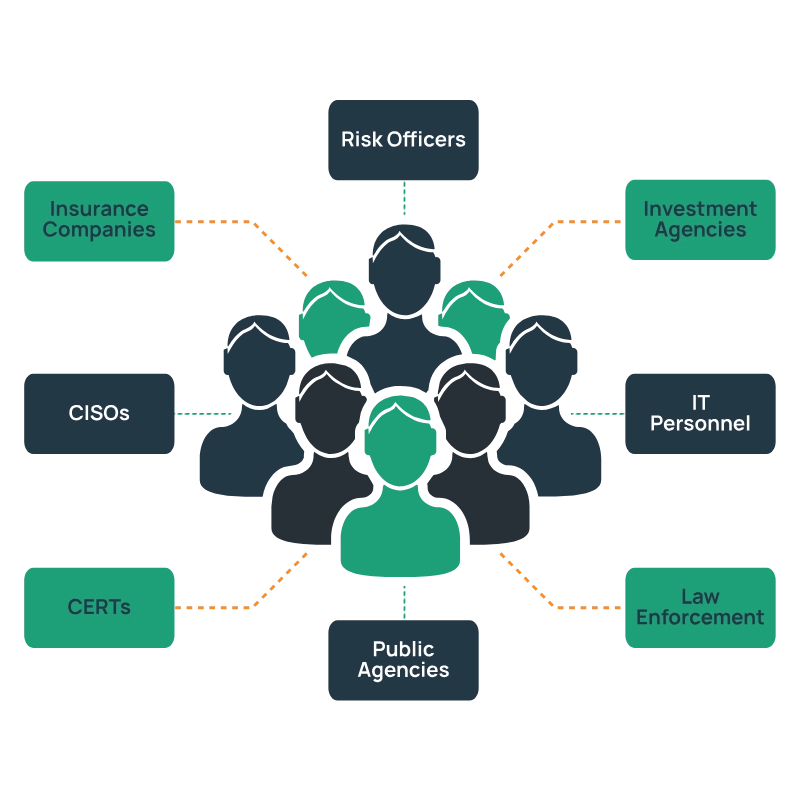
Who is IT meant for?
Game-changing Insights
Calculate the risk values of enterprises, governments, NGOs, educational institutions, vendors and suppliers or their customers.
You no longer need to calculate the company risk based on external information, paper documentations or audits – which are oftentimes outdated and inaccurate nevertheless.
Factors such as infection rates, malspam campaigns and ransomware efforts provide valuable insights into your own or third-party cyber risk exposure, enabling you to address these challenges effectively within a single solution.
unmatched coverage of cyber incidents
Achieve true Resilience & NIS2-Compliance.
With the power to predict the next moves of your adversaries, you don’t need to be afraid of weaknesses that could cause you irrevocable damage or compromise your compliance with the NIS2 Directive.
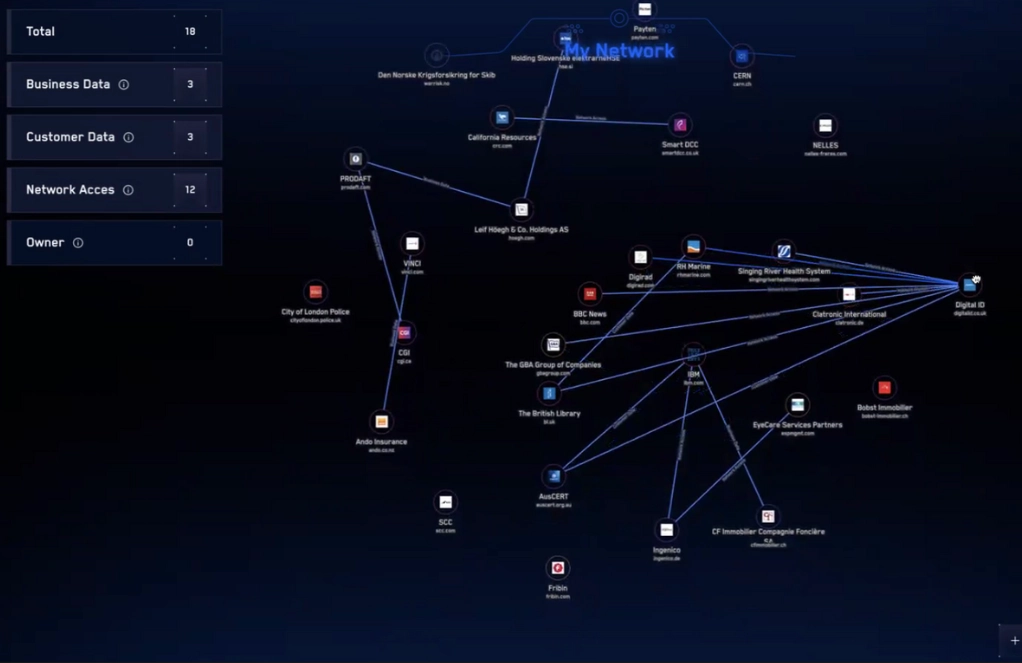
Instead, it allows you to see an already-established connectivity graph with the risk networks that are relevant to your organization.
You can always adjust the intelligence sources via your Priority Intelligence Requirements, depending on your unique needs and objectives.